What is scanned?
Docker image security scans look for vulnerable OS packages installed in your Docker images on supported Linux distributions:- Debian / Ubuntu: packages installed using
dpkgor itsapt-getfrontend. - CentOS / Red Hat / Amazon Linux: packages installed using
rpmor its frontendsyumanddnf. - Alpine Linux: packages installed using
apk.
- packages installed from source (e.g., using
make && make install). - packages installed by language-level package managers, such as
bundler,npm,pip,yarn,composer,go install, etc. (third-party vulnerability analysis providers support those, and you can incorporate them using a CI process, for example).
FAQ
How do I access security scans?
How do I access security scans?
Access Docker image security scans in the Aptible Dashboard by navigating to the respective app and selecting “Security Scan.”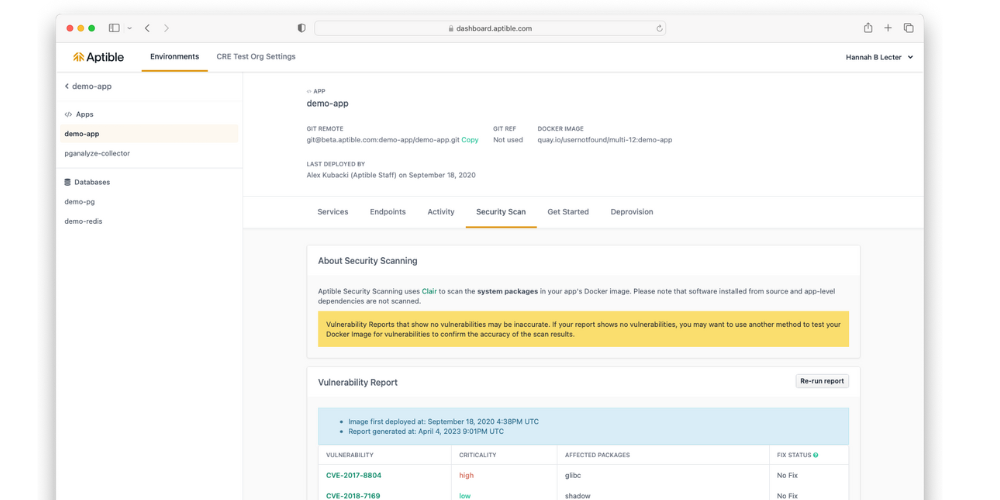

What OSes are supported?
What OSes are supported?
Ubuntu, Debian, RHEL, Oracle, Alpine, and AWS Linux are currently supported.Some operating systems, like CentOS, are not supported because the OS maintainers do not publish any kind of security database of package vulnerabilities.
You will see an error message like “No OS detected by Clair” if this is the case.
What does it mean if my scan returns no vulnerabilities?
What does it mean if my scan returns no vulnerabilities?
In the best case, this means that Aptible was able to identify packages installed in your container, and none of those packages have any “known” vulnerabilities.In the worst case, Aptible is unable to correlate any vulnerabilities to packages in your container.Vulnerability detection relies on your OS maintainers to publicly publish vulnerability information and keep it up to date.
The most common reason for there being no vulnerabilities detected is if you’re using an unsupported (e.g., End of Life) OS version, like Debian 9 or older, for which there is no longer any publicly maintained vulnerability database.
How do I handle the vulnerabilities found in security scans?
How do I handle the vulnerabilities found in security scans?

