Company
Feb 24, 2017
Aptible was not affected by Cloudbleed
Aptible was not affected by Cloudbleed

Frank Macreery
CEO
Some have suggested that Cloudflare might not be a HIPAA business associate because of an exception to the definition of business associate known as the “conduit” exception. Cloudflare is almost certainly not a conduit. HHS’s recent guidance on cloud computing takes a very narrow view:
The conduit exception applies where the only services provided to a covered entity or business associate customer are for transmission of ePHI that do not involve any storage of the information other than on a temporary basis incident to the transmission service.
OCR hasn’t clarified what “temporary” means or whether a CDN would qualify, but again, almost certainly not, as data storage is a critical, non-incidental component of CDN functionality.
What if I used Cloudflare to cache PII?
Again, activate your incident response plan and talk to your lawyer. HIPAA is just one of many data privacy regulations. Many states require companies to report breaches of personally identifiable information belonging to residents of that state.
What if I used Cloudflare for data aside from PHI or PII?
We encourage you to be safe and rotate all credentials that might have passed through Cloudflare from your app, such as session cookies, API keys, and user passwords.
What else should I do?
We encourage you to rotate your passwords for any service that used Cloudflare between September 22, 2016, and February 18, 2017. Cloudflare has not released a list of services affected. You can find one security researcher’s list of Cloudflare DNS customers (which is likely overinclusive) here.
Some have suggested that Cloudflare might not be a HIPAA business associate because of an exception to the definition of business associate known as the “conduit” exception. Cloudflare is almost certainly not a conduit. HHS’s recent guidance on cloud computing takes a very narrow view:
The conduit exception applies where the only services provided to a covered entity or business associate customer are for transmission of ePHI that do not involve any storage of the information other than on a temporary basis incident to the transmission service.
OCR hasn’t clarified what “temporary” means or whether a CDN would qualify, but again, almost certainly not, as data storage is a critical, non-incidental component of CDN functionality.
What if I used Cloudflare to cache PII?
Again, activate your incident response plan and talk to your lawyer. HIPAA is just one of many data privacy regulations. Many states require companies to report breaches of personally identifiable information belonging to residents of that state.
What if I used Cloudflare for data aside from PHI or PII?
We encourage you to be safe and rotate all credentials that might have passed through Cloudflare from your app, such as session cookies, API keys, and user passwords.
What else should I do?
We encourage you to rotate your passwords for any service that used Cloudflare between September 22, 2016, and February 18, 2017. Cloudflare has not released a list of services affected. You can find one security researcher’s list of Cloudflare DNS customers (which is likely overinclusive) here.
Some have suggested that Cloudflare might not be a HIPAA business associate because of an exception to the definition of business associate known as the “conduit” exception. Cloudflare is almost certainly not a conduit. HHS’s recent guidance on cloud computing takes a very narrow view:
The conduit exception applies where the only services provided to a covered entity or business associate customer are for transmission of ePHI that do not involve any storage of the information other than on a temporary basis incident to the transmission service.
OCR hasn’t clarified what “temporary” means or whether a CDN would qualify, but again, almost certainly not, as data storage is a critical, non-incidental component of CDN functionality.
What if I used Cloudflare to cache PII?
Again, activate your incident response plan and talk to your lawyer. HIPAA is just one of many data privacy regulations. Many states require companies to report breaches of personally identifiable information belonging to residents of that state.
What if I used Cloudflare for data aside from PHI or PII?
We encourage you to be safe and rotate all credentials that might have passed through Cloudflare from your app, such as session cookies, API keys, and user passwords.
What else should I do?
We encourage you to rotate your passwords for any service that used Cloudflare between September 22, 2016, and February 18, 2017. Cloudflare has not released a list of services affected. You can find one security researcher’s list of Cloudflare DNS customers (which is likely overinclusive) here.
Some have suggested that Cloudflare might not be a HIPAA business associate because of an exception to the definition of business associate known as the “conduit” exception. Cloudflare is almost certainly not a conduit. HHS’s recent guidance on cloud computing takes a very narrow view:
The conduit exception applies where the only services provided to a covered entity or business associate customer are for transmission of ePHI that do not involve any storage of the information other than on a temporary basis incident to the transmission service.
OCR hasn’t clarified what “temporary” means or whether a CDN would qualify, but again, almost certainly not, as data storage is a critical, non-incidental component of CDN functionality.
What if I used Cloudflare to cache PII?
Again, activate your incident response plan and talk to your lawyer. HIPAA is just one of many data privacy regulations. Many states require companies to report breaches of personally identifiable information belonging to residents of that state.
What if I used Cloudflare for data aside from PHI or PII?
We encourage you to be safe and rotate all credentials that might have passed through Cloudflare from your app, such as session cookies, API keys, and user passwords.
What else should I do?
We encourage you to rotate your passwords for any service that used Cloudflare between September 22, 2016, and February 18, 2017. Cloudflare has not released a list of services affected. You can find one security researcher’s list of Cloudflare DNS customers (which is likely overinclusive) here.
Latest From Our Blog
Thoughts & Ideas
HIPAA on PaaS: Vercel, Render, Heroku, Railway, and Aptible

Gabriella Valdes
Customer Success

Thoughts & Ideas
HIPAA on PaaS: Vercel, Render, Heroku, Railway, and Aptible

Gabriella Valdes
Customer Success

Thoughts & Ideas
HIPAA on PaaS: Vercel, Render, Heroku, Railway, and Aptible

Gabriella Valdes
Customer Success

Thoughts & Ideas
HIPAA on PaaS: Vercel, Render, Heroku, Railway, and Aptible

Gabriella Valdes
Customer Success
Company
Aptible in 2024: Year in Review

Frank Macreery
CEO

Company
Aptible in 2024: Year in Review

Frank Macreery
CEO

Company
Aptible in 2024: Year in Review

Frank Macreery
CEO

Company
Aptible in 2024: Year in Review

Frank Macreery
CEO
Changelog
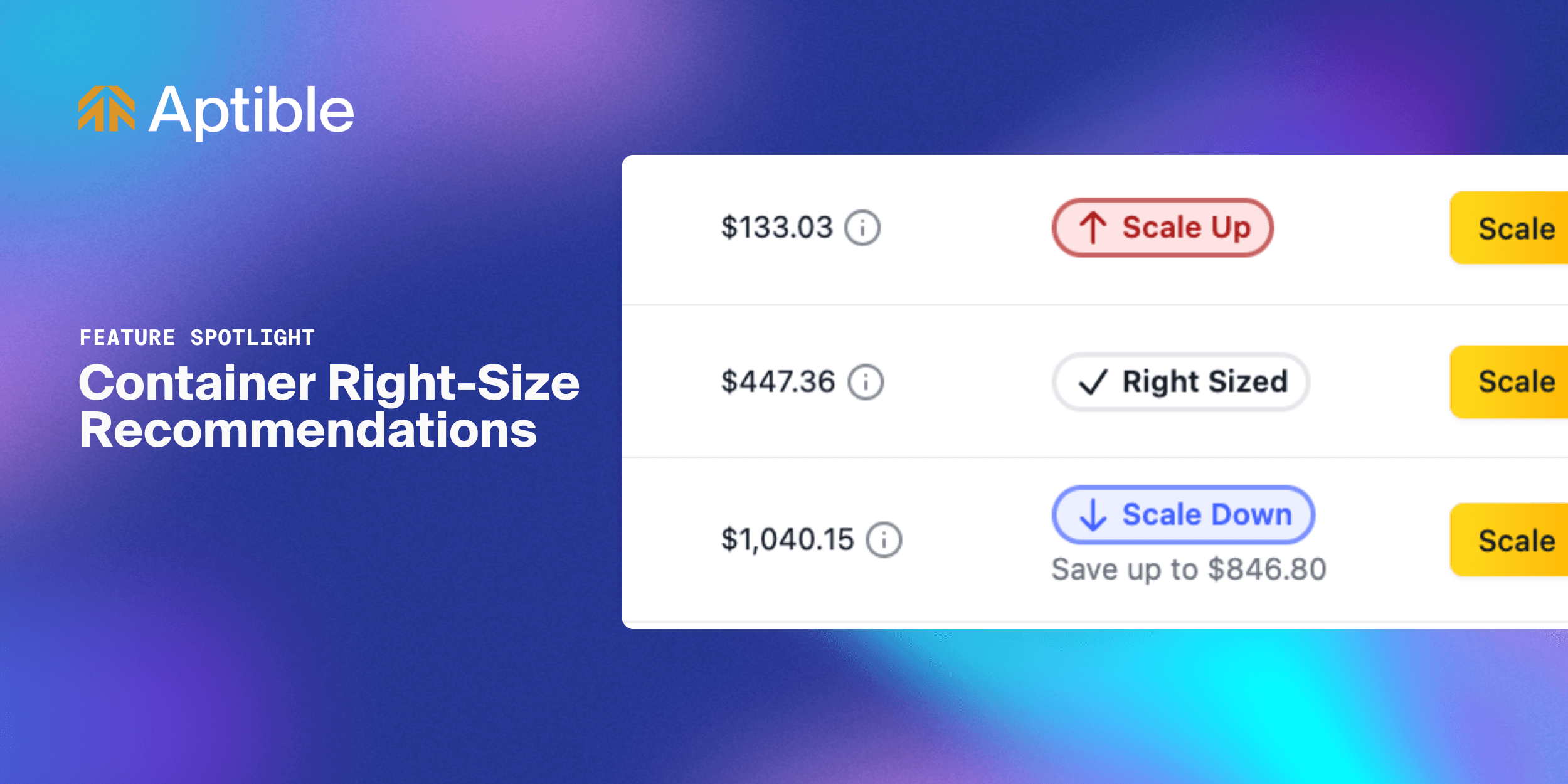
Introducing Container Right-Size Recommendations for Apps and Databases

Gabriella Valdes
Customer Success

Changelog
Introducing Container Right-Size Recommendations for Apps and Databases

Gabriella Valdes
Customer Success

Changelog
Introducing Container Right-Size Recommendations for Apps and Databases

Gabriella Valdes
Customer Success

Changelog
Introducing Container Right-Size Recommendations for Apps and Databases

Gabriella Valdes
Customer Success




548 Market St #75826 San Francisco, CA 94104
© 2025. All rights reserved. Privacy Policy
548 Market St #75826 San Francisco, CA 94104
© 2025. All rights reserved. Privacy Policy
548 Market St #75826 San Francisco, CA 94104
© 2025. All rights reserved. Privacy Policy
548 Market St #75826 San Francisco, CA 94104
© 2025. All rights reserved. Privacy Policy
